In the age of digital transformation, healthcare organisations face a new kind of emergency — one that originates not from patient illness but from malicious digital threats. Protecting patient data from cyber threats is now a mission-critical goal for every enterprise hospital. As attacks become more sophisticated, only a secure hospital management system can safeguard sensitive information, ensure compliance, and maintain uninterrupted operations. This is where a cyber-resilient Hospital Management System (HMS) becomes indispensable to modern healthcare IT security.
The Urgent Case for Cyber Resilience in Hospital Management Systems
Global hospitals generate massive volumes of patient data daily. Each digital record carries personal and financial information that cybercriminals target aggressively. Cyber security healthcare strategies must therefore evolve beyond basic firewalls and antivirus tools. A hospital management system equipped with advanced HMS cyber threat protection for hospitals ensures that every digital transaction, medical record, and clinical workflow remains secure.
The growing threat landscape—ransomware, phishing, and unauthorised data access—demands continuous monitoring and proactive defence. Enterprise hospitals cannot rely on outdated systems. They need a hospital management system that is intelligent, adaptive, and built to detect and neutralise threats in real time.
Protecting Patient Data from Cyber Threats: The Strategic Priority
Enterprise hospitals operate on a foundation of trust. Patients expect that their data remains safe at all times. Hence, protecting patient data from cyber threats is not just an IT function but a leadership priority. A breach impacts not only regulatory compliance but also the reputation and continuity of care for large-scale operations.
Multi-Layered Defence: Securing Data Through a Robust HMS
A hospital management system (HMS) built with multi-layered security protocols is essential. This architecture ensures that every piece of data—clinical, diagnostic, or financial—remains secure across departments and throughout its lifecycle. To achieve long-term resilience, every enterprise hospital must integrate healthcare IT security policies directly into its hospital management system architecture.
Key Security Advantages of HMS-Based Data Protection
A robust HMS provides critical features that elevate data security beyond basic measures. These integrated capabilities are non-negotiable for enterprise-level defence:
- Encrypted Communication: Ensuring encrypted communication between hospital systems to prevent interception.
- Real-Time Auditing: Continuous monitoring of access logs and data activity for immediate transparency and accountability.
- Predictive Analytics: Integration of predictive analytics for early threat detection and proactive defence.
- Automated Lockdowns: Implementing automated system lockdowns during suspicious access attempts to contain breaches instantly.
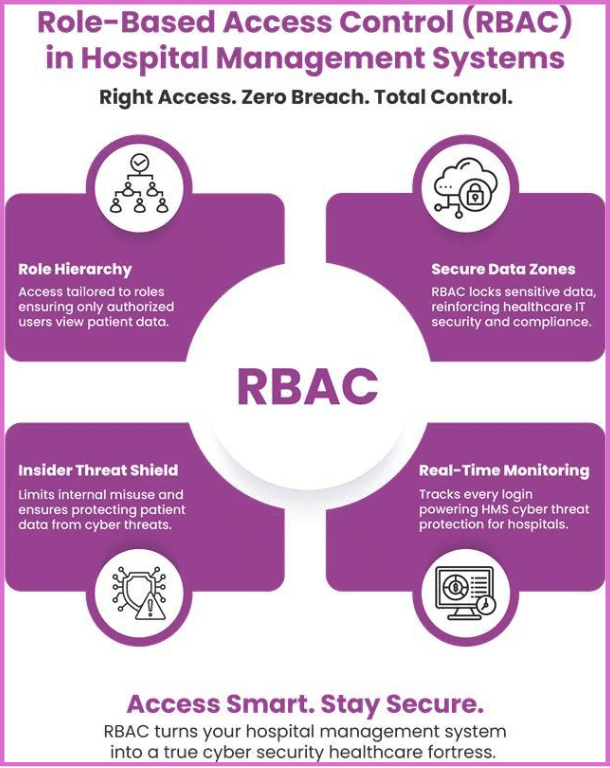
Role-Based Access Control in Hospital Management System Security
A critical element of cyber security healthcare for large institutions is ensuring that only authorised personnel can access sensitive patient data. This is achieved through Role-Based Access Control (RBAC) in a hospital management system. RBAC is not merely a security feature; it is a vital operational tool that strictly limits permissions according to defined staff responsibilities.
For instance, doctors access clinical data and treatment plans, billing teams view financial and administrative records, and IT administrators manage security protocols. This granular segmentation ensures that staff only interact with the data necessary for their job functions, streamlining workflows while significantly reducing exposure.
This strategic segmentation strengthens HMS cyber threat protection for hospitals by effectively eliminating the risk of internal misuse and maintaining absolute data integrity. By defining clear boundaries for data interaction, enterprise hospitals leverage RBAC to achieve high operational efficiency while simultaneously meeting and maintaining strict healthcare IT security compliance standards. A well-implemented RBAC system is, therefore, foundational to securing the entire patient information ecosystem.
Also Read – The Role of Clinical Management Systems In Improving Patient Outcomes – Ezovion.
Hospital Data Breach Prevention Through a Secure HMS Framework
Data breaches can cost hospitals millions in losses and reputation damage. The most effective defence lies in a hospital management system designed for breach prevention. Enterprise hospitals that deploy a cyber-resilient HMS enjoy enhanced control over data flow, end-point protection, and secure authentication layers.
Hospital data breach prevention involves:
- End-to-end encryption of patient data
- AI-driven anomaly detection
- Regular vulnerability testing
- Automated alerts for unauthorised access attempts
When combined, these features form the backbone of HMS cyber threat protection for hospitals, ensuring the continuity of care without compromising patient privacy. Every CIO must prioritise these protocols to maintain healthcare IT security excellence.
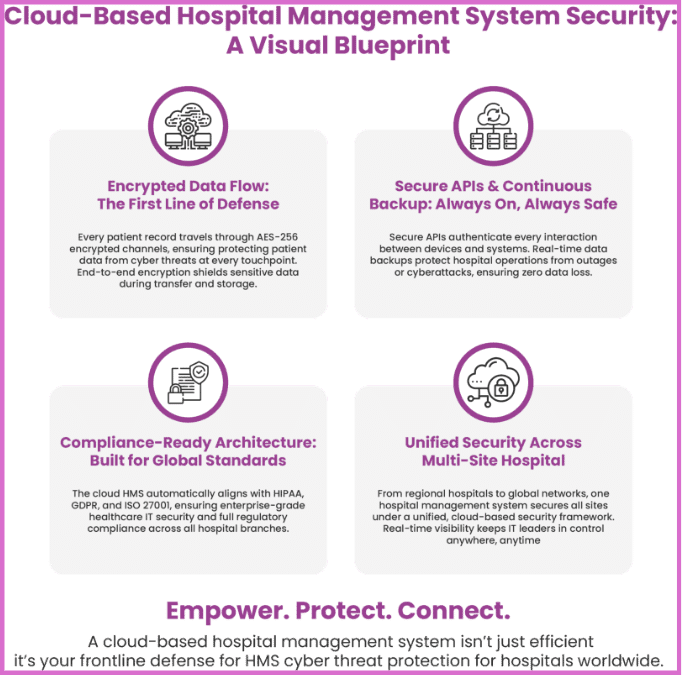
Cloud-Based Hospital Management System Cyber Security
The shift toward cloud-based solutions has revolutionised cyber security healthcare. A cloud-based hospital management system provides agility, scalability, and stronger data protection compared to traditional on-premises solutions. Cloud encryption and access controls minimise vulnerabilities and ultimately reduce maintenance costs for enterprise hospitals. This modern architecture empowers healthcare leaders to focus on innovation while maintaining airtight HMS cyber threat protection for hospitals.
Enhancing Healthcare IT Security with Cloud HMS Benefits
A well-implemented cloud architecture delivers distinct advantages critical for large-scale healthcare operations and compliance. These features ensure robust and continuous protection:
• Centralised Threat Monitoring: Enables seamless, round-the-clock threat detection and management across all hospital and clinic locations.
• Disaster Recovery and Data Redundancy: Ensures immediate data redundancy and backup capabilities essential for rapid disaster recovery and business continuity.
• Multi-Layered Encryption and Integration: Provides multi-layer encryption alongside secure API integrations to safeguard data exchange and system connectivity.
• Automated Vulnerability Patching: Delivers automatic updates to patch new cyber vulnerabilities instantly, removing the burden from internal IT teams.
Also Read – Ezovion On-Prem Hospital Management Solutions – Ezovion.
Hospital Medical Device Security Integration with HMS
Connected medical devices (IoMT) form the backbone of modern healthcare delivery—from patient monitoring systems to infusion pumps. However, this proliferation also creates significant and often overlooked vulnerabilities that threat actors actively exploit. Addressing this risk is crucial, which is why hospital medical device security integration with HMS is now a fundamental requirement for enterprise resilience. By treating these devices as extensions of the core system, hospitals can drastically reduce their attack surface.
Integrating device protection directly with the hospital management system (HMS) helps safeguard these critical assets and the patient data they transmit. This strategic approach ensures that security protocols are centralised and consistently applied across the entire technological ecosystem, moving beyond traditional network perimeters. This unified method effectively fortifies cyber security healthcare across the board.
Achieving this level of comprehensive security relies on implementing several secure device integration strategies. These strategies include robust device authentication before data exchange and mandating encrypted data transfer between devices and HMS. Furthermore, integration must provide centralised visibility for IT security teams to monitor all connected devices in real time and enable automated threat isolation for compromised devices.
Ultimately, this essential integration extends HMS cyber threat protection for hospitals beyond traditional IT boundaries, encompassing every endpoint that touches patient care. This unified, proactive stance is vital for maintaining operational continuity and safeguarding highly sensitive clinical environments.
Compliance and Global Healthcare IT Security Standards
Enterprise hospitals must adhere to stringent compliance frameworks such as HIPAA, GDPR, and regional data privacy laws. A compliant hospital management system simplifies these processes by automating documentation, audit logs, and data handling workflows.
Compliance-driven HMS capabilities:
- Policy-based access restrictions
- Secure data archiving
- Automated compliance reporting
- Real-time governance dashboards
Embedding these capabilities ensures healthcare IT security remains consistent across multiple sites and jurisdictions, supporting global operations and trust-building with patients.
The Future of Cyber Security Healthcare: AI, Blockchain, and Zero-Trust Systems
The future of cyber security healthcare lies in convergence — where AI, blockchain, and Zero-Trust frameworks form the ultimate defence. A future-ready hospital management system will use AI for continuous monitoring, blockchain for transparent data integrity, and Zero-Trust models to validate every connection.
These technologies redefine HMS cyber threat protection for hospitals, enabling digital ecosystems that are both secure and intelligent. Enterprise hospitals must invest in these next-generation systems to sustain growth, resilience, and innovation.
Building the Future of Secure Healthcare
Healthcare leaders must act decisively. The urgency of protecting patient data from cyber threats defines the future of digital healthcare. A hospital management system that integrates comprehensive HMS cyber threat protection for hospitals empowers organisations to operate securely in an increasingly volatile environment.
Strong healthcare IT security not only prevents attacks but also strengthens patient confidence and operational excellence. The enterprise hospitals that invest today in cyber security healthcare will build the digital fortresses that define tomorrow’s trusted care institutions.





