
Heath IT Companies and solutions in the medical industry have already made life easier for doctors and patients alike. However, the problem of patient data privacy continues to be a source of contention. Even modern medical software’s security measures cannot guarantee data safety from cybercriminals and insider threats.
When handwritten data is transformed with electronic medical records to keep a steady flow of patient-related info: personal details, diagnosis, treatment, and follow-ups, data security becomes a major concern.
These archives are mostly hosted on open-source platforms or unsecured hospital management system with electronic medical record software, making them easily accessible and downloadable. With such easy access to patients’ information, it is even more critical to protect their data in order to avoid misuse of sensitive and private information.
Let’s go to this article to know how the Healthcare IT Companies overcome with these challenges click here.
The Role of Hospital Information Management Software Providers in Protecting Sensitive Patients’ Medical Records in Heath IT Companies
The power to automate the concealing of sensitive patient medical records gives payers, providers, and patients the assurance that data is just shared with those who need it. Content that addresses patient codes comprehensively is an important component of any technological infrastructure aimed at the precise and efficient classification and filtering of sensitive data.
Educate Hospital IT Company Staffs on Workplace Cybersecurity Policy
When it comes to your healthcare practice’s cybersecurity in hospitals, hospital employees are your weakest link. The entire hospital or clinic can go offline with just one click on a phishing email or one simple password easy to hack.
Educating staff members about cybersecurity best practices as soon as they begin working will support the development of a culture of individual accountability. This includes:
- Log off computers when not in use.
- How to safely send sensitive information to colleagues.
- Finding and isolating phishing links and emails
- Passwords that are at least 16 characters long.
- Periodic password changes
Enforce Role-Based Access & Security
When all hospital employees have access to all patient data, you run the risk of an employee with ulterior motives leaking the information. Furthermore, you increase the chances of a hacker locating a staff with access to a specific account. Hence implement hospital information management software which offers a high level of security features and role-based access to the HIMS software.
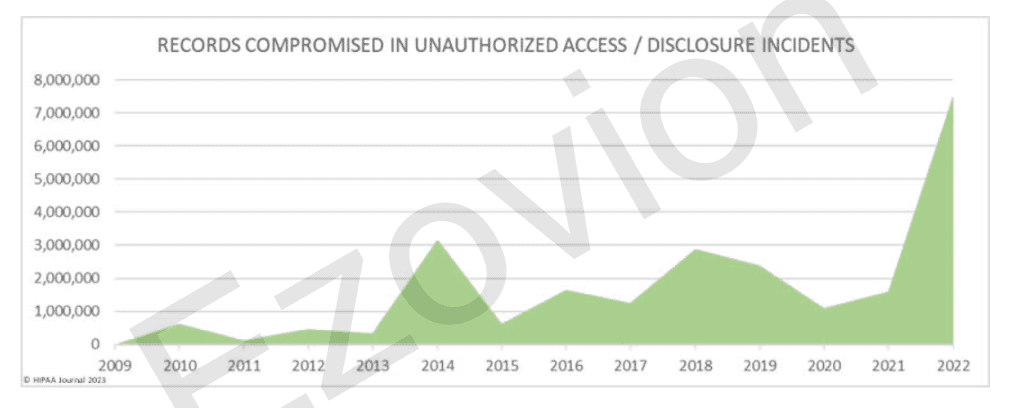
Implementing role-based security procedures reduces the risk of sensitive patient medical records being leaked or stolen, prevents employees with malicious intent from accessing any data they want, and keeps your hospital/clinic HIPAA compliant by preventing employees from randomly accessing sensitive patient data they aren’t authorized to.
Assign different levels of access controls to healthcare professionals and hospital staff based on how critical it is for them to have access to that data.
Strong Anti-Virus specially for Heath IT Companies
Malicious malware or viruses have the potential to corrupt your software and data. The hospital management software provider can include features that allow for timely alerts and reminders.
The anti-virus software should be able to identify, scan the computer for malicious code, and provide a thorough analysis of what every file consists in terms of the potential risks involved with that specific programme, which is extremely effective at preventing the spread of infections throughout networks.
Data Backup
All hospitals are obligated to keep their information safe and secure, but having sensitive healthcare data on their hospital management software makes this even more critical.
With a good backup policy, healthcare IT Companies can help with safeguarding and securing valuable data. Even if something unfortunate occurs, a good backup policy can protect you from loss of data and help you maintain business continuity. Cloud-based hospital management system would take care of automated database backup for faster recovery process and minimize downtime.
Data theft and Monetization in Heath IT Companies
As cybercriminals target health care facilities more frequently, stolen and revealed medical records may expose patients to scams and even lead in fraudulent activity.
Hackers Love Medical Records
Medical records are popular targets for hackers because they are a goldmine of all these details about you. They comprise a patient’s names, address, financial data, enough information for cybercriminals to take out a loan or open a credit line in the patients’ names.
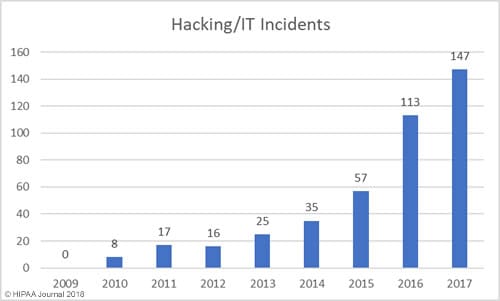
Fig: Hacking incidents (Source- HIPAA Journal 2018)
Hackers also target health records since hospitals and health-care facilities are frequently easy to compromise. As a result, it is relatively simple for such hackers to obtain a significant amount of personal info for medical fraud.
Monetization
On the black market, hackers’ profit from selling the information. Buyers may use the medical data to create fake IDs to purchase hospital supplies or drugs, or to file a falsified insurance settlement.

All of the records can be expensive. A patient’s complete medical records can fetch up to $1,000. Credit card information, on the other hand, typically sells for $1 and can go up to $110.
Because of the high costs, hackers will go to extreme lengths to obtain medical records.
Ways to mitigate the risk in Heath IT Companies
Preventing hospital database breaches in healthcare can be difficult and often requires additional funding, but it may save your organization from larger problems, such as a loss of reputation, in the long run. The following are the most important tasks you can do to sharpen up your systems.
Identifying the Right HIMS Software Vendor
Patients’ medical data theft is not just by hackers, sometime the data could be stolen by hospital information management software vendor as well. The vendors wanted to make quick money sell the hospital software for free or cheap but sell patient data for profit from selling the information.
Identify a vendor with
- A vendor who is specialized in healthcare industry only
- Proper privacy policy
- Data encryption & Security measures
- Check their portfolio.
- Products, solutions, and price
- Look for companies with a strong track record.
- Check for reviews, ask for referrals.
- Customer testimonials
- Look for a company that has been in business for several years.
- Look for a company that has a strong reputation.
- Look for a company that offers a money-back guarantee.
Analyze current security threats for Heath IT Companies
HIPAA requires Hospital Management Software providers to conduct a yearly security risk evaluation for finding vulnerabilities and policy review. Prioritize regular security audits without skipping or reducing them.
Don’t ever avoid educating your employees
Make certain that your staff fully comprehend the implications of a security breach in healthcare, in addition to the various kinds of data breaches. They must also be aware of indicators for both preventing and dealing with threats.
Make subnetworks
Consider segmenting your wireless network into subnetworks for various user groups, like patients, visitors, employees, and medical devices. In other words, give guests public wi-fi access that is separate from your private network where patient information is being circulated.
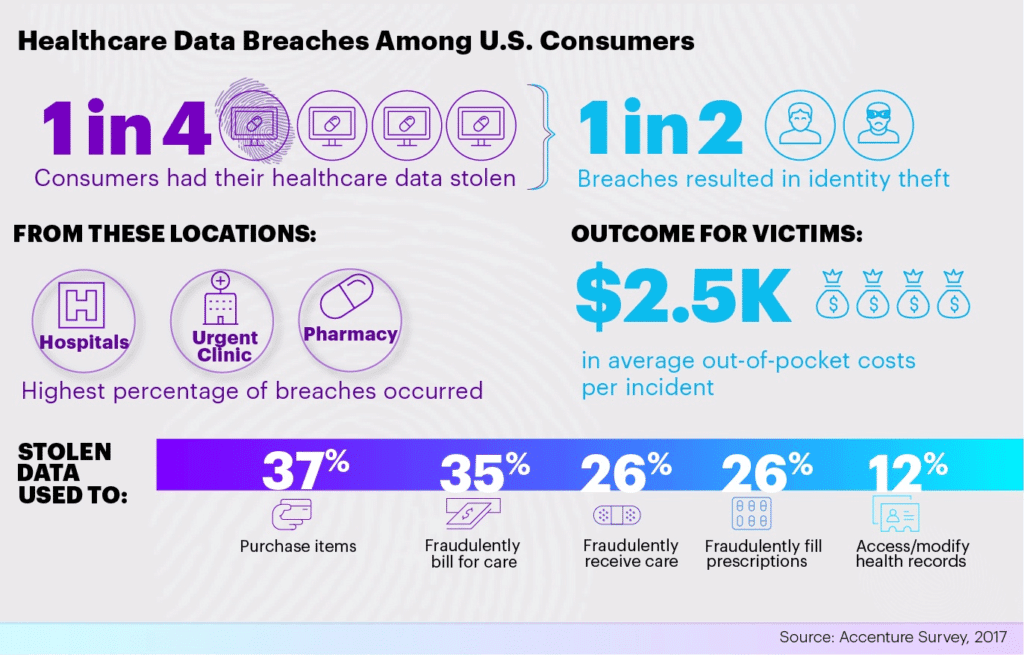
Refrain from utilizing dated IT infrastructure
The older your infrastructure, the more likely it is that hackers will gain access to it. To decrease the chance of patients’ medical data breaches, replace outdated devices on a regular basis.
Data encryption
Hospital database encryption technologies will assist you in mitigating the effects of cyberattacks. Because encrypted data is not considered unsecured under HIPAA’s Breach Notification Rule, encrypted data loss does not entail a breach. As a result, while you’ll still have to deal with the incident, encryption can save you from potential government penalties.
Limit the use of personal devices
Healthcare professionals frequently use personal devices for quick network access, but this introduces new risks because malware infiltrates the system, making it vulnerable to attacks. If you allow your employees to bring their own mobiles or other electronic devices to work, develop a strict and clear policy outlining which devices they can use both inside and outside the network, how to link them to the network, and so on.
Restriction on access to medical records
With hundreds of individuals and devices within a healthcare organization, it’s essential to identify users, monitor their activity, and ensure proper logging in and out procedures. Examine your access permissions based on user position to ensure that only health providers who work with health records have access to them.
Conclusion
Customized hospital management systems are far more resilient to cyberattacks than off-the-shelf solutions. However, it is critical to select an HMS Provider with experience in health – care development and information security.
Ezovion is Premium Hospital Management System that can be customized to the needs of the healthcare facility. We provide
- Cloud-based infrastructure will also comply with HIPAA and GDP requirements by regularly updating products and equipment and monitoring the system for potential vulnerabilities and suspicious activity.
- Encryption – Two-key encryption systems are another tool that can enhance the safety of stored data. With geographically diverse storage and high-level encryption, your data security improves.
- Backups – Ezovion HMS instantly backs up your data, so you can be confident that it will not be lost.
To secure your medical data more efficiently visit us and book a free trail!





